Using Trusted Applications
Overview of Trusted Applications
Trusted Applications with Registered Applications
Trusted Applications without Registered Applications
Supported Authentication Mechanisms
|
•
|
|
•
|
Early Binding
Process Diagram
|
4.
|
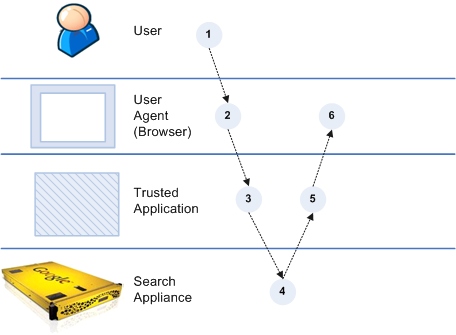
If trusted applications is enabled and trusted applications are registered: In this mode, the trusted application forwards the secure search request to the search appliance using trusted user credentials together with the end user’s ID. The search appliance verifies the trusted application.
Internally, the security manager gets the credentials from the request and verifies them. After the normal authentication check, the security manager checks to see if the request is from a trusted application by checking against the trusted application user names and/or group. If so, it creates a verified end-user session for the end user. There is no more credential gathering from the end user's agent. The search appliance uses the end user (X_GSA_USER and X_GSA_CREDENTIAL_GROUP headers) during the next phase (group resolution and authorization). If trusted applications is enabled, but no trusted applications are registered: In this mode, the user’s credentials are sent to the security manager. It verifies the end user’s credentials, which are used for authorization. |
Setup for Using Trusted Applications
Set up your environment to use the trusted applications feature by performing the following tasks:
|
•
|
Setting up Universal Login by using the Search > Secure Search > Universal Login page, as described in Universal Login.
|
|
•
|
Configuring a credential group for basic authentication or cookie authentication for trusted applications by using the Search > Secure Search > Universal Login Auth Mechanisms page, as described in HTTP-Based Authentication, and Cookie-Based Authentication.
Take note that the trusted applications feature does not support multiple credential groups. |
|
•
|
|
•
|
After set up is complete, start using secure search with your trusted applications.
Enabling and Registering Trusted Applications
Trusted applications is disabled by default on the search appliance.
To enable trusted applications:
|
1.
|
In the Admin Console, click Search > Secure Search > Trusted Applications.
|
|
2.
|
Click Enable Trusted Applications.
|
To register trusted applications:
|
1.
|
In the Admin Console, click Search > Secure Search > Trusted Applications.
|
|
2.
|
|
3.
|
|
5.
|
|
6.
|
Click Save.
|
For more information about how to register trusted applications, click Admin Console Help > Search > Secure Search > Trusted Applications.
Configuring Your Trusted Application
If no trusted applications are registered, do not use X_GSA_USER and X_GSA_CREDENTIAL_GROUP headers. Otherwise, a 502 error is returned.
X_GSA_USER: Header
The X_GSA_USER: header is required. It identifies the end user that the trusted application is performing the search for. This field can also include a domain, as shown in the following examples:
X_GSA_USER:user1
X_GSA_USER:user1@my_company.com
X_GSA_CREDENTIAL_GROUP: Header
The X_GSA_CREDENTIAL_GROUP: header is required. It identifies the credential group that the end user is associated with, as shown in the following example:
X_GSA_CREDENTIAL_GROUP:TAUsersCredGroup
Search Query Formats
Cookie Authentication
If cookie authentication is used, the search query can be in one of the following formats:
curl -b "<cookie_name>=<cookie_value>" --header "X_GSA_USER:<user_name>"
--header "X_GSA_CREDENTIAL_GROUP:<credential_group_name>"
"http://www.mycompany.com/search?q=YOUR_QUERY_HERE&access=a"
where <cookie_value>=application's cookie
curl -b "<GSA_SESSION_ID>=<session_id>;<cookie_name>=<cookie_value>"
--header "X_GSA_USER:<user_name>"
--header "X_GSA_CREDENTIAL_GROUP:<credential_group_name>"
"http://www.mycompany.com/search?q=YOUR_QUERY_HERE&access=a"
where <session_id>=application's GSA_SESSION_ID returned as a set cookie form a previous request
Basic Authentication
If basic authentication is used, the search query can be in one of the following formats:
curl --user user_name:password --header "X_GSA_USER:<user_name>"
--header "X_GSA_CREDENTIAL_GROUP:<credential_group_name>"
"http://www.mycompany.com/search?q=YOUR_QUERY_HERE&access=a"
curl -b "<GSA_SESSION_ID>=<session_id>" --user user_name:password
--header "X_GSA_USER:<user_name>"
--header "X_GSA_CREDENTIAL_GROUP:<credential_group_name>"
"http://www.mycompany.com/search?q=YOUR_QUERY_HERE&access=a"
where <session_id>=application's GSA_SESSION_ID returned as a set cookie form a previous request
POST Support for Long Queries
Google recommends that you use the HTTP POST request with trusted applications, especially if your query strings exceed the 2KB URL length limit of GET requests. If you use a GET request, the query string is truncated if it exceeds the limit. Truncation might occur when you submit dynamic navigation queries containing a large number of metadata filters. You can avoid this limitation by submitting POST requests instead, which have a much larger body limit (10KB). However, using the GET request is also an option.
Take note that, for secure searches, POST requests can only be used with trusted applications. They cannot be used with secure search requests that do not use trusted applications. This type of search request only uses the GET command.
For more information on this topic, see Using the POST Command in the Search Protocol Reference.