What is UPnP?In the digital world, the technique is riddled by security vulnerabilities caused by flaws in software design. The introduction of Universal Plug and Play (UPnP) was hailed as a tremendous scientific advance. However, it has some disadvantages that could escape your systems vulnerable to computer hackers. In reality, thousands of routers have facilitated it by default. This article explains what UPnP is and the privacy concerns it raises to your system. Definition of UPnP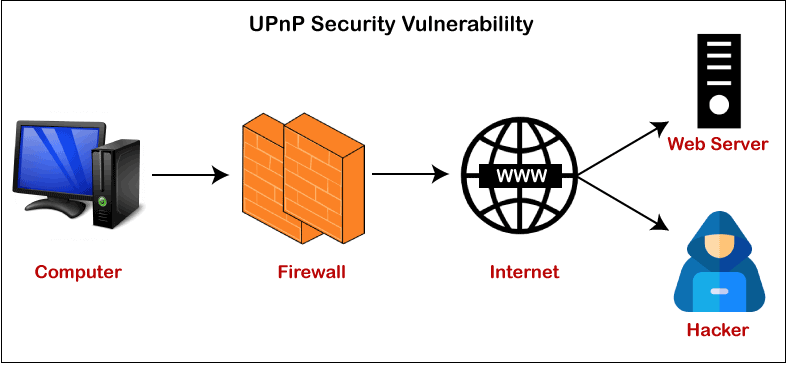
A positioned of networking protocols known as Universal Plug and Play (UPnP). It allows system components like computer systems, Security processes, scanners, streaming server, and Wi-Fi cognitive framework to explore each other's prime time and generate proposed neural services such as data exchange. UPnP was designed for secure networks without innovation interconnection. This innovation assumes that a system model IP (Internet Protocol), during which it uses XML, SOAP, and HTTP and provides service/device summary, packet forwarding, behavior, and racing. Commercials and hardware query demands are allowed using HTTPMU to operate HTTP concerning UDP - port 1900. (multicast). Respondents to search queries are typically sent via UDP. The UPnP site, a business project to encourage robust approach interconnection to desktop computers and hold equipment from multiple retailers, supported this innovation. The panel included over 800 retailers specializing in everything from computer clusters to electronic products. However, as of 2016, the Accessible Interconnection Framework manages Universal Plug and Play. Universal Plug and Play (UPnP) is expected to improve plug and play (an innovation that adaptively enables communication to a device) to negligible communication for SOHO and townhomes wireless networks. As a result, UPnP phones are the prototypical plug-and-play. When connected to the internet, they pursue and generate required to work setups with other equipment. What is the purpose of UPnP?If the initial concept seemed a little complicated, consider a computer as an instance. In an office environment, the first phase would be to securely touch it to the wireless router - although it is now possible to do so via Wi-Fi. Previously, you had to start searching for the scanner and then configure it to find other devices on a network. Once linked, the technologies on that system will contact one another by transmitting or receiving data. As a result, a desktop can inform the order to print files, a cable box can send audio data, and smartphones can install themselves on the desktop. The options are limitless. It is why it is referred to as plug-and-play. You insert in a machine and immediately begin trying to play it without need to go through the hassle and cost of establishing and managing the link. As a result, it is one of the most efficient networking technological innovations to us. UPnP technique, on the other hand, has significant vulnerabilities. For example, if a group of computers connected to the network is compromised, the intruder may obtain a game controller over all machines and safety systems. As a result, availability to your logins and availability to all other network-connected devices is granted. Furthermore, once a machine has been breached, it can be used as a portion of malware to launch distributed denial of service (DDoS) initiatives against websites while concealing the assailant's destination. It could also serve as a springboard for other threats. With ever more interfaces using this innovation to access the internet, they are optimal targets for attackers who need to gather devices to overpower a local business. The Security Dangers of Universal Plug and Play
According to an Akamai security survey, attackers aggressively manipulate this tech's flaws as a jumping-off point for more influential assaults. Malware allocation, DDoS, credit card fraud, and malware emails are just a few examples. According to the intelligence obtained, over four million interfaces were extremely vulnerable to being used in a Cyberattack. This figure represents an estimated 38% of the 11 million worldwide web UPnP apps in use around the globe. It provides a massive pool for attackers to utilize businesses and micro assaults into major threats. Largely, these fraudsters take advantage of these digital technology flaws to repetitively redirect congestion in the company until it becomes completely undetectable. Moreover, despite the company's awareness of these flaws, attackers attempt to abuse the general lack of interest in enhancing innovation. This innovation does not use verification by the switch. It indicates that to maintain security, the channel's interfaces must include the providing Instruction Security Agency or Device Defense Agency. A non-standard solution is available as well, recognized as Universal Plug and Play - User Name (UPnP-UP), which suggests an addition to facilitating user systems and information methodologies for UPnP-applications and technologies. Unfortunately, most global plug-and-play hardware architectures lack secure protocols because they presume local devices and their customers can be accepted. Security systems and adapters that use the UPnP procedure that become resistant to threats if material facts are not used. The threat of Universal Plug-and-playAfter all, this ease of use creates an opportunity for attackers. In the scenario of Mirai, it permitted them to inspect for these terminals before hacking into the machine on the other side. Attackers have discovered an even more nefarious application for UPnP with the trojan horse Pinkslipbot, also identified as QakBot or QBot. QakBot has been infecting computers since 2000, installing a keystroke logger and then sending account information to secluded Command and Control (C2) servers. What is a C2 server?It is a discreet strategy to post-exploitation because it makes it more difficult for IT safety to detect any irregularities. Even so, to an administrator or technologist observing the network, the customer appears to be internet browsing - although the RAT is obtaining integrated instructions to sign logins or lookup for Personally identifiable information (PII) and manipulating login credentials, credit card details, and other sensitive information to the C2s. The best deterrent is to control the sites of recognized C2 hiding places. After all, the hackers play a cat-and-mouse game, looking for new dark patches on the Internet to establish their data centers as older models are processed by organizational security people. And this is where Pinkslipbot has made a major contribution. For lack of better words, it has presented center-malware, which afflicts computers but does not steal login credentials! Conversely, the center-malware sets up a VPN C2 server that sends HTTPS requests to the actual C2 servers. 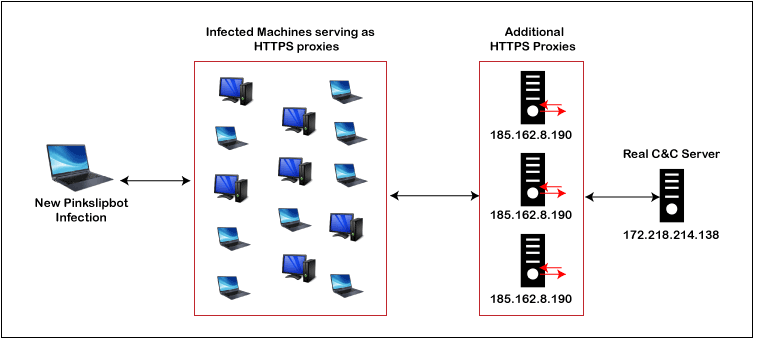
As a result, the Pinkslipbot equipment does not have a specified web address for their C2 databases. In influence, the entire World serves as their field of play! It makes it virtually impossible to keep a database of current domain names or identifies to scan out. What is the connection between UPnP and Pinkslipbot?When the Pinkslipbot takes control of a customer's laptop, it verifies whether UPnP is turned on. If it is, the Pinkslipbot center-malware sends a UPnP (Universal Plug-and-Play) request to the router, requesting that a social port be opened. It enables Pinslipbot to behave as a circuit between the RAT-infected machines and the attacker's C2 servers. It's nefarious, and we can reluctantly give these people a (black) hat tip. We can all do to make such sorts of threats more complicated to carry out to deactivate the UPnP or port-forwarding functionality on our home networks. You most likely do not require it! Working of UPnPUPnP implies that a machine is IP-addressable for using safety procedures developed on it, such as HTTP (HyperText Transfer Protocol), XML (Extensible Markup Language), Transmission Control Protocol), and User Datagram Protocol (UDP). These procedures are used to promote the computer's appearance and for data transmission. It connects to UDP packets 1900. Addressing
Simple Service Discovery Protocol (SSDP)SSDP is the procedure that UPnP technologies are using to explore one another.
Summary of the deviceWhen technologies reveal each other, they share information in Xml file to understand about one another. These texts include data such as the maker's title, product id, maker webpages, services offered by the machine, specifications or assertions to be carried to the machine for a service, and so on. Service RequestsAfter obtaining information on the device as well as its facilities, the control panel can request the provider via the URL given by the customer, which functions similarly to a coding function call. This is accomplished through the use of the Simple Object Access Protocol (SOAP), which transports XML texts. Architecture for General Event Notification (GENA)The GENA architectural style is used in UPnP for incoming messages. Facilities also use it to react to customer inquiries. A control point can adhere to a phone's notification; each machine has a set of Product factors that, when changed, notify the coordinate system. These texts will be sent in Xml file as well. PresentationA machine may include a URL to the company's website for demonstration; this will be used by a checkpoint to extract data and also by the customer to personalize the settings menu in an internet browser. Don't Ignore Network SecurityUniversal Plug and Play strategy's goal is to make systems on a particular network easily recognizable by other facilities on the similar network. Regrettably, some Universal Plug and Play (UPnP) control modules can be revealed to the corporate network, allowing cyber criminals to retrieve and connect to your systems. A compromised device is nothing more than a disaster waiting to happen for your corporate servers. Due to the extreme complexity of these assaults, identifying one as it occurs can be extremely difficult for the customer. In today's world, where a liquid workplace culture is optimal, an increasing number of staff is bringing access points to and from task. When it relates to the company's information security, there is no margin for mistakes. The lesson to be learned here is that you should deactivate your UPnP (Universal Plug-and-Play) router configurations. Benefits of UPnP
Drawbacks of UPnP
Next TopicList of Inorganic Compounds
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share










